I had hoped that the survey would be distributed to as many people in the club as possible to view the staff’s attitudes towards cyber security. However, as it happened, most clubs provided a single response, usually from the manager (71% of respondees). Sixty-eight staff members from 60 golf clubs answered the survey, presented in five sections looking at general information, knowledge of cyber standards and initiatives, attitudes towards future cyberattacks, how email links and attachments are processed, and knowledge of passwords and password management.
1. General information
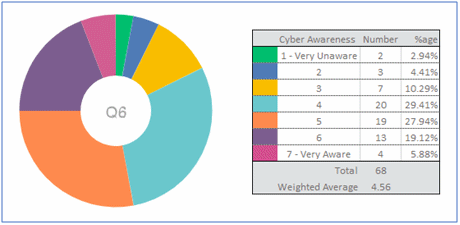
Fifty-six people thought they were from average to very cyber aware, and the weighted average over the seven-point sales was 4.56. Over half of the respondents scored themselves five or higher. The inference from this is that managers feel they are well equipped to defend the club against cyber attacks.
It may be no surprise that over 70% of respondents were aged over 50, though there was no discernable bias in any of the answers related to age.
Six clubs (10%) admitted to suffering an attack. But, more interestingly, 26 respondents did not know if an attack had taken place. I would expect some office staff to be unaware of whether an attack had occurred, but this indicates even some managers are unaware.
2. Knowledge of cyber awareness initiatives and cyber standards
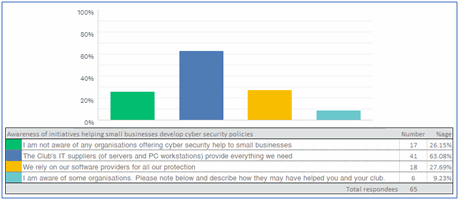
This section was revealing. The government in the form of GCHQ and the National Cyber Security Centre (NCSC.gov.uk – the public arm of GCHQ) charged with “Helping to make the UK the safest place to live and work online” has spent a lot of effort and money promoting cyber security safety and standards to small businesses and yet 26% were completely unaware of any initiatives while a vast 70% relied on their hardware and software suppliers to look after cyber security matters for them. Only six respondees admitted any knowledge, and no one had heard of any NCSC schemes!
The lack of knowledge of cyber standards and initiatives is reflected by only 30% of clubs having a cyber security policy. This is worrying as best practice dictates that such a policy and response plan should be in place. However, the good news is that those who have a policy in place found implementing it not difficult.
3. Chances of a successful cyber attack in the next 12 months
The Government’s Cyber Security Breaches Survey 2020 found that almost half of businesses (46%) suffered a cyber breach in the year up to winter 2019. Respondents think their chances of being attacked are relatively low at 3.0/7, with phishing attacks through email attachments (3.5/7) and malicious links (3.8/7) being the most likely successful attack vector.
4. Attitude and behaviour towards emails
Most respondents (84%) know what a phishing email is and can accurately describe the threats it poses. However, fifty-three respondents rarely or never click on a link or download an attachment. While this is likely to mitigate a cyber-attack, it does mean that a potentially valid link or attachment is overlooked. The Golf Club Secretary newsletter (April, p127) provides ways to identify the validity of links and attachments. Managers within clubs may well understand the seriousness of phishing attacks, but other staff with access to email through the club’s systems may not. Small businesses are subjected to over 65,000 phishing emails a day, with one success every 19 seconds. Fraudsters are becoming ever more sophisticated. They carefully research their intended victims so they can make any email look genuine (The Golf Club Secretary Newsletter: March p115 and April p127).
5. Knowledge of password strength and password management
This section looked at weak and strong passwords, how passwords are used and how they are managed. Everyone recognised that 12345 was a weak password; however, 21 respondents (35%) did not identify Password1# as weak. Looking at strong passwords, over a third (36.7%) considered gOLFcLUB55! to be strong and four managers thought John1971! was strong. (The Golf Club Secretary newsletter: May, p129).
Good practice dictates that passwords are never shared with others and never used on more than one site, yet fifty respondents reuse and twenty-two share passwords!
The final question in the survey looked at how people managed passwords. A quarter of respondents use a password manager, with a further 13% storing passwords in a web browser. Other options involved keeping passwords in files or paper, using a limited number that is easy to remember, or using a technique that creates a memorable, unique password for all sites.
6. Conclusions
The survey was completed mainly by managers or senior people in clubs. It, therefore, did not garner information and attitudes from people who worked in the office or other areas of the club where technology is in place. Consequently, these results reflect management’s attitudes to human cyber awareness in clubs.
This conclusions are interesting. Managers tend to think they are cyber-aware. GDPR training from two years ago, the annual health and safety sessions and anecdotal incidents may have been an influence. Yet, the results indicate a lack of cyber awareness. For example, email links and attachments tend not to be opened as a matter of course, potentially ignoring important messages. In addition, the way passwords are used and managed is open to cyber attacks. And, there is an over reliance on their hardware and software suppliers to provide all the cyber protection needed. You trust them to protect you at a technical level. However, some malicious cyber activity will break through their barriers. Are you and your staff effective human firewalls? There are many resources available on the Internet and a good starting point is ncsc.gov.uk.
Paul is happy to assist and answer any questions you may have regarding cyber security in your club’s environment, so please feel free to contact him at paul@sawted.com if you have and questions.