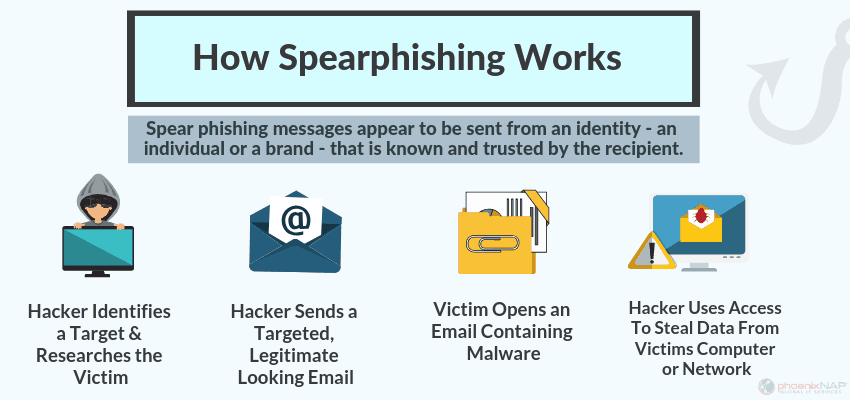
Let us look more closely at phishing or, more specifically, spear-phishing, what it is and how the fraudsters trick you into clicking on a link or downloading an email attachment. Most common phishing attacks are blocked by your internet service providers, anti-virus software and software providers. But spear-phishing is a little different, and these emails are far more likely to evade your hardware and software defences and appear in your inbox. In case you think clubs are not a target, remember that you have both staff and many members, providing a broad attack surface.
Small businesses are subjected to over 65,000 phishing emails a day, with one success every 19 seconds. Fraudsters are becoming ever more sophisticated. They carefully research their intended victims so they can make any email look genuine. Some even find out your family’s, friends’ and pets’ names, what your interests are, and where you go on holiday. They may take months to gather such information, so they know a lot about you. Then the fraudster uses all kinds of psychological means to trick you. He may place you under time pressure, tell you how to secure a substantial government or council grant or frighten you by saying you have not paid a fine. It may be an email that looks as if it has come from one of your suppliers or members. Fraudsters’ campaigns are targeted. They want to trick or con you into reacting. Once you have clicked on a link or downloaded an attachment, the fraudsters have you speared, hence the term spear-phishing.
As a manager, you will be aware of the issues and attempt to instil a cautious attitude to emails in your staff. But, genuine mistakes will happen, and when they happen, any malware may spread laterally to all systems in the club’s network. Recovery from a failure costs money, takes time and damages the club’s reputation.
While we know that we should be wary about clicking on a link or downloading an attachment, some are genuine and needed for our jobs. Distinguishing the bad from the good is a skill in its own right. Technology can help to an extent but cannot safeguard you against everything. Here are three simple human-related defences against phishing attacks.
- Double-check who the email is from. The email header may say it is from John Smith, but when you check the sender’s actual address, you see that it is from someone or somewhere completely different. Your spam filters will not necessarily stop them all, so it is always a good idea to “check before you click”.
- Some links are incorporated within the text of the message. For instance, click here to find out more, or click here to get the latest report. To check it out, let the cursor hover over the link but do not click the mouse. The full address will be displayed. Do you know it? Is the link secure (https://…)? Does it look sensible?
- Check if any link address given in full looks genuine. For example, https://www.hmrc-refund.com is not a safe address as all UK government addresses will end in .gov.uk. However, https://www.refund.HRMC.gov.uk is a subdomain of HMRC and is genuine. It is also possible that a link that looks good, such as https://www.hmrc.gov.uk, is hiding a different address. Hover over it, and you will see it reveals a different destination!
Defending against these phishing threats involves making people aware of the risks and giving them the knowledge and tools to protect themselves. The trouble Is that people may be diligent in checking emails after training but will revert to old habits over time. Consequently, an ongoing testing and education programme is needed for you and your staff to become a human firewall against phishing attacks.