The bad guys are using ever more sophisticated means to get your login credentials to access your personal information and gain access to the club’s data. Yes, there are still thousands of immediately recognisable phishing emails used by amateur criminals. But, the clever criminals are now carefully researching us and then targeting us with highly plausible ‘spear phishing’ emails tricking even the most cautious of us to click on a malicious email link. The recent Human Cyber Awareness survey has highlighted that managers generally consider themselves cyber aware, yet 75% do not have a cybersecurity policy and over 90% rely on the club’s hardware and software suppliers to protect them. What about all the other staff at the club who have access to the club’s systems? We are all fallible and can click on a malicious email link. Phishing emails either take us to an authentic-looking login page for the site we think we wish to log into or download malware onto our computers which may then spread throughout the club. Either way, the results are good for criminals but not for us.
We protect ourselves and our information with passwords. They help authenticate us to websites and applications. The survey shows that we tend to reuse passwords across multiple sites (84%), even sharing some of them with colleagues (41%). 123456 holds the number one spot in the most used password lists (Nordlink, SplashData and the U.K.’s National Cyber Security Centre). Qwerty, senha, 1q2w3e4r are all in the top 20, along with sunshine, princess, iloveyou and password. Do you use any of these passwords? Be honest here.
Password Strength
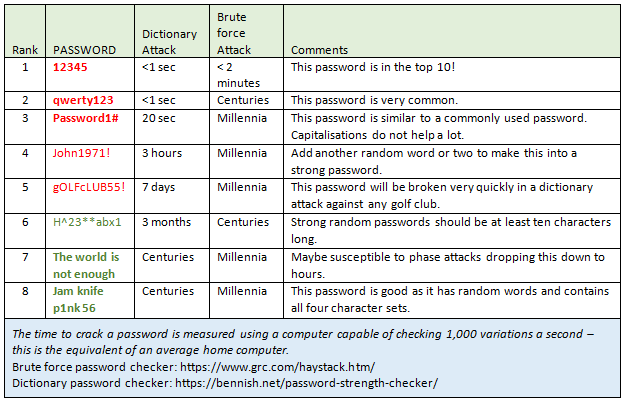
Strong passwords are vital. Simple passwords may easily be guessed or broken by criminals. The two main types of attack are ‘brute force’ and ‘dictionary’. Brute force attacks look at every combination of characters that may make up a password. This type of attack requires high-speed computers and can take a very long time. Consequently, criminals often employ dictionary attacks instead. These attacks start with a dictionary of common words and phrases. The criminals then use tools to extract all the unique words on your social media pages and websites and add them into the source dictionary. These attacks are more efficient and yield results in a fraction of the time. The table below compares the time taken to crack a password using a dictionary against using brute force.
Multi-Factor Authentication (MFA)
Password strength is one defence, but a second and powerful defence is MFA. If the website we log onto uses MFA, then the first time we log onto it, a message is sent to our email address or mobile phone. Hence the two factors – our password plus a second method. MFA dramatically improves security at the cost of a little more effort on our part. Some websites, such as online banking, require MFA every time you log onto their systems. Others need it for the first time you use their website from a specific computer or web browser.
All accounts involving money must use MFA for obvious reasons. Email accounts should always have MFA activated. If criminals have access, they can change your password and then impersonate you and attack all your contacts.
Password Managers (PWM)
Password managers are great friends in the fight to secure data and identity. PWMs can store thousands of random solid passwords only used when a recognised website is accessed. Only one strong password or passphrase is needed to access the PWM. The passwords are available across all devices, from computers to mobile phones, making it simple to log on securely to websites. Passwords are encrypted and stored using robust encryption methods that even the CIA and GCHQ would find hard to crack. And PWMs have two other unique capabilities providing even more robust security. The PWM can give a password only to a site that is known to it. Therefore if a criminal manages to lure you to a website asking for your credentials, it will not be recognised by the PMW, and the password not revealed. Because the password is passed to a website directly, keylogging malware cannot see it and send it back to the criminals. PWMs are not expensive, though ignore any that are free. Some highly regarded password managers are 1Password, LastPass, Keeper and Roboform.
In conclusion, If there are two things that everyone should now do, they are to: start using Multi-Factor Authentication; and buy and use a decent Password Manager. These two steps will provide a solid defence against criminals’ gaining access to your personal information and the club’s sensitive data.
